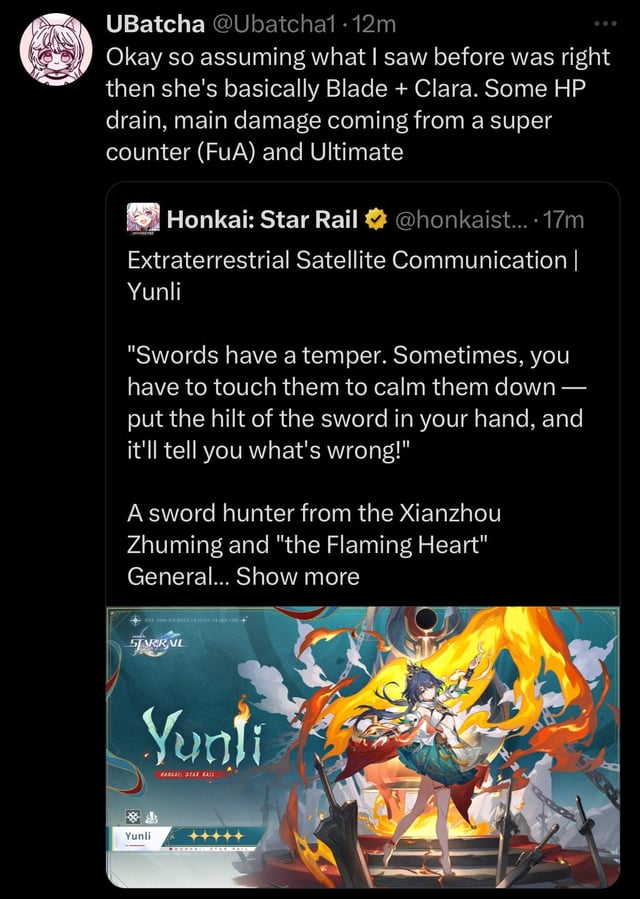
Okay, so today I’m gonna spill the beans on something I stumbled upon – yunli kit leaks. Buckle up, it’s gonna be a bumpy ride.
How I Found It:
It all started when I was messing around with some old debugging tools. I was trying to reverse engineer some code for a personal project. Basically, I was poking around and trying to see what I could find. I started by setting up my usual environment, nothing fancy, just some virtual machines and emulators. Then, I downloaded a few of the yunli kits to test some theories.
I fired up my debugger, attached it to a running process, and started stepping through the code line by line. I was using some fuzzing techniques to try and identify areas where the application might be vulnerable.
Deeper Dive:
As I dug deeper, I noticed some strange behavior. Some APIs that shouldn’t be exposed were visible and accessible. That’s when I realized something was seriously wrong. The more I looked, the more I found. Turns out, there were some serious misconfigurations that were leaking a ton of sensitive information.
- API keys
- Secret tokens
- Internal IP addresses
- Database credentials
Basically, the whole shebang! It was like finding a treasure trove of information that should have been locked away tight.
The Impact:
I realized the potential damage this could cause was huge. With this kind of information, someone could:

- Access internal systems
- Impersonate users
- Steal data
- Generally wreak havoc
My Response:
First thing I did was stop what I was doing. I knew this was way bigger than my little side project. I immediately started documenting everything I found. I created a detailed report with all the evidence, including screenshots, code snippets, and logs.
Then, I tried to figure out the right way to report it. I spent a good chunk of time trying to find a security contact or a bug bounty program. Eventually, I found a contact email and sent them the report.
The Aftermath:
To their credit, they responded pretty quickly. They confirmed they were looking into it and thanked me for reporting it. They took the information seriously and got to work fixing the vulnerabilities.
A few weeks later, they got back to me and said they had patched the leaks. They also gave me a shout-out in their security bulletin, which was pretty cool.
Lessons Learned:
This whole experience taught me a lot about security and the importance of proper configuration. Here are a few key takeaways:

- Always double-check your configurations.
- Implement proper access controls.
- Regularly audit your systems.
- Have a clear process for reporting vulnerabilities.
Final Thoughts:
It’s a wild world out there, and security is a constant game of cat and mouse. Stay vigilant, keep learning, and don’t be afraid to dig deep. You never know what you might find.